As organizations accelerate AI adoption, they’re racing to inventory data, classify sensitive assets, and implement governance frameworks. Naturally, DSPM adoption is on the rise.
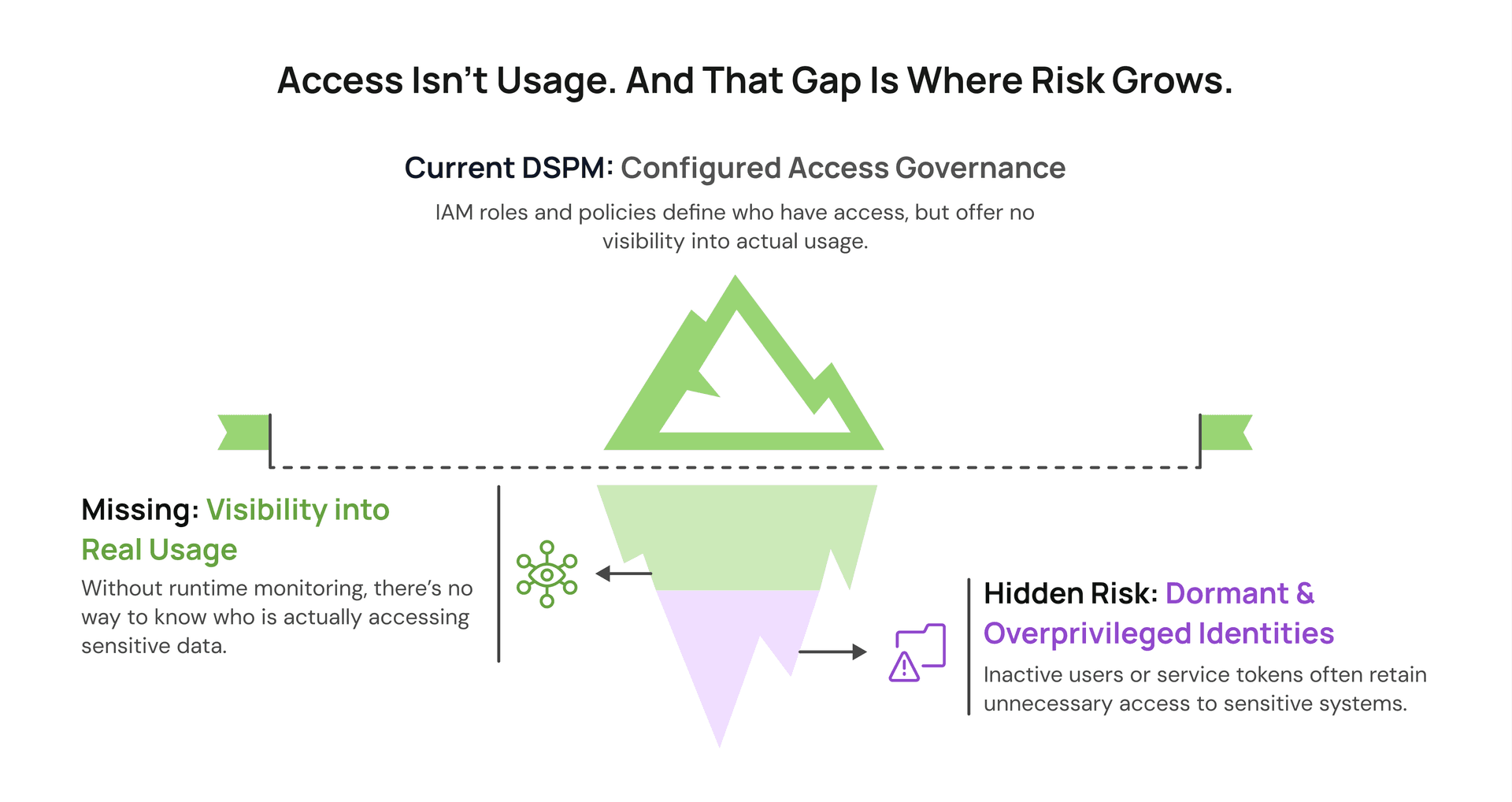
But here’s the catch: DSPM remains largely a governance tool. It answers foundational questions like: Where does my sensitive data live? Who can access it? Is it properly classified and encrypted?
These are critical, but incomplete. Many CISOs we’ve spoken with raise the same concern: DSPM often falls short on continuous value and actionability. Knowing where data resides and who can access it is useful; but without context on actual usage, it’s hard to decide what to fix, revoke, or prioritize.
To truly secure data in today’s AI-powered, hybrid environments, you need more than visibility into static policies and permissions. You need insight into actual behavior.
DSPM tools operate like well-maintained blueprints: they tell you how access is designed. But attackers and insider threats don’t care about how your IAM policies are structured on paper. They exploit how things work in practice.
For example:
Without runtime monitoring, these scenarios fly under the radar.
To mitigate risk and enforce true least privilege, you need both:
When Access Governance and Monitoring are combined, it together unlocks:
This combination transforms DSPM from a static asset inventory into a dynamic risk engine.
Many teams assume they’re secure once they’ve reviewed access policies and passed compliance audits. But policies don’t guarantee protection.
The real risk lives in what happens after deployment — when applications and identities interact with sensitive data in unexpected ways. That’s the blind spot DSPM doesn’t see.
Runtime monitoring fills this gap. It shows which identities are using which permissions, where data is flowing, and whether usage aligns with expectations. Not after the fact, but as it happens.
In modern AI systems, data moves constantly — between services, clouds, teams, and vendors. Static governance doesn’t keep pace. You need visibility into real behavior.
Zero Trust isn’t achieved through policy alone. It requires continuous verification. And that means monitoring real access patterns, not just provisioning logic.
When governance (what’s allowed) and monitoring (what’s happening) are connected, you can:
- Identify unused or risky access
- Enforce least privilege at runtime
- Minimize the impact of compromised identities or misconfigurations
This is how organizations move from theoretical compliance to active enforcement, and from guesswork to real control.
DSPM is a vital step in data security maturity. But relying on it alone is like setting your house rules without checking if they’re followed. True data protection comes from combining data access governance with data access monitoring.
Because attackers don’t care about your policies. They care about the gaps. And you can’t close those gaps if you can’t see them.

USA
AURVA INC. 1241 Cortez Drive, Sunnyvale, CA, USA - 94086
India
Aurva, 4th Floor, 2316, 16th Cross, 27th Main Road, HSR Layout, Bengaluru – 560102, Karnataka, India
PLATFORM
Solutions
Integrations

USA
AURVA INC. 1241 Cortez Drive, Sunnyvale, CA, USA - 94086
India
Aurva, 4th Floor, 2316, 16th Cross, 27th Main Road, HSR Layout, Bengaluru – 560102, Karnataka, India
PLATFORM
Solutions
Integrations

USA
AURVA INC. 1241 Cortez Drive, Sunnyvale, CA, USA - 94086
India
Aurva, 4th Floor, 2316, 16th Cross, 27th Main Road, HSR Layout, Bengaluru – 560102, Karnataka, India
PLATFORM
Solutions
Integrations